Amazon GuardDuty EKS Protection
Amazon GuardDuty is designed to protect AWS workloads from various security threats by analyzing events, data, and activity across AWS accounts. With a focus on providing real-time threat detection, GuardDuty helps users stay one step ahead of potential security risks. By leveraging machine learning and AWS's extensive threat intelligence, GuardDuty identifies suspicious behavior and alerts users about potential security issues.
Amazon GuardDuty for EKS brings the same level of protection to containerized environments. By continuously monitoring EKS clusters, GuardDuty helps ensure that your container workloads are shielded from malicious activities and unauthorized access attempts.
Integrating Amazon GuardDuty with EKS offers several benefits for enhanced security, with a focus on both EKS Audit Log Monitoring and EKS Runtime Monitoring.
EKS Audit Log Monitoring
Amazon GuardDuty's EKS Audit Log Monitoring plays a critical role in identifying and mitigating security threats by analyzing and alerting administrators about potential risks related to EKS cluster configurations and control plane activities.
Enhanced Threat Identification: Amazon GuardDuty continuously monitors EKS audit logs for any misconfigurations that might expose the cluster to vulnerabilities. This includes unauthorized access attempts, changes to cluster settings, and API calls that deviate from standard patterns. By identifying these anomalies, Amazon GuardDuty helps administrators stay vigilant and quickly respond to potential security breaches.
Proactive Security: With Amazon GuardDuty, administrators receive real-time alerts when suspicious activities are detected in the audit logs. This proactive approach empowers teams to take immediate action and prevent security incidents.
EKS Runtime Monitoring:
Amazon GuardDuty's EKS Runtime Monitoring focuses on the runtime environment of EKS clusters, analyzing container and pod behavior to detect anomalies, malicious activities, and potential compromises.
Automated or Manual Agent Setup: Amazon GuardDuty simplifies the process of setting up agents for EKS clusters. Administrators can choose to deploy the GuardDuty agent automatically or manually, depending on their preference and requirements. Automated agent setup ensures seamless integration, allowing administrators to focus on security rather than cumbersome deployment procedures.
CPU and Memory Monitoring: Amazon GuardDuty provides insights into CPU and memory usage patterns within EKS clusters. Unusual spikes in resource utilization can indicate unauthorized access or malicious activities. By monitoring these metrics, GuardDuty aids administrators in identifying potential threats and resource abuse.
Runtime Event Types: Amazon GuardDuty comprehensively analyzes various runtime event types, including unauthorized pod creations, privilege escalations, and unexpected container executions. These insights enable administrators to understand the full scope of potential security incidents and take appropriate actions.
By leveraging EKS Audit Log Monitoring and EKS Runtime Monitoring, organizations can benefit from a holistic security approach, ensuring comprehensive coverage of their EKS clusters and containerized workloads. Amazon GuardDuty's real-time alerts, proactive threat detection, and deep visibility into EKS environments enable administrators to maintain a secure and robust containerized infrastructure on AWS.
GuardDuty Findings for EKS
Amazon GuardDuty generates various types of findings specific to EKS clusters, providing valuable insights into potential security risks. These findings fall into two main categories: Runtime Findings and Audit logging Findings. You can see the most important main finding types below.
Amazon GuardDuty EKS Audit Logging Findings
EKS audit logs provide detailed insights into the activities within your Kubernetes cluster. These logs help you understand who did what and when, which is crucial for security and compliance.
Unauthorized Access Attempts: Amazon GuardDuty can detect audit logging findings related to unauthorized access attempts, such as failed login attempts using invalid credentials or attempts to access resources that a user or application shouldn't have permissions for.
Sensitive Resource Access: EKS audit logs can reveal if there are attempts to access sensitive resources or perform privileged operations. Amazon GuardDuty can help identify patterns of behavior that might indicate unauthorized access to critical data or configurations.
Pod Security Policy Violations: If your EKS cluster enforces Pod Security Policies (PSPs) to ensure containers adhere to security standards, audit logs can help identify instances where pods violate these policies. Amazon GuardDuty can flag such violations, helping you maintain a secure container environment.
Cluster Configuration Changes: Changes to your EKS cluster's configuration can impact security. Audit logs can help you keep track of modifications to settings, roles, and permissions. Amazon GuardDuty can alert you for unusual or unauthorized configuration changes.
Anomalous User Behavior: Amazon GuardDuty can identify abnormal user behavior based on audit logs. For example, if a user suddenly starts accessing resources they've never accessed before or performing actions they don't typically perform, this could be an indicator of a compromised account.
Amazon GuardDuty EKS Runtime Findings
Amazon GuardDuty is a threat detection service that continuously monitors for malicious activity and unauthorized behavior within your AWS environment, including Amazon EKS (Elastic Kubernetes Service) clusters. It helps you identify security threats by analyzing events, flows, and other data sources.
Unusual Process Activity: Amazon GuardDuty can detect runtime findings related to unusual or suspicious process activity within your EKS nodes. This detection includes identifying processes attempting to establish unauthorized network connections, executing suspicious code, or performing actions outside of their typical behavior.
Privilege Escalation: Amazon GuardDuty monitors for attempts to escalate privileges within your EKS environment. This might involve detecting unauthorized attempts to gain elevated permissions or access resources that an application or user shouldn't have access to.
Network Connections: Amazon GuardDuty can identify network connections that might be indicative of a security breach or unauthorized access attempt. For EKS, this could involve detecting unexpected network connections between containers, pods, or nodes.
You can see detailed findings for EKS Runtime Finding types here.
Understanding these different types of findings allows administrators to prioritize security response efforts and take prompt action to mitigate potential threats. By addressing these findings and implementing security best practices, organizations can maintain a robust and secure EKS environment, safeguarding their containerized applications and data from various security risks.
Integrating Amazon GuardDuty with Amazon EKS for Account and Organization-Level Protection
In this section, I will talk about how you can manage GuardDuty on one account and multiple organization accounts.
Enable Amazon GuardDuty Service:
- Go to the AWS Management Console.
- Navigate to the Amazon GuardDuty service.
- Enable GuardDuty for the AWS region where your EKS cluster is located.
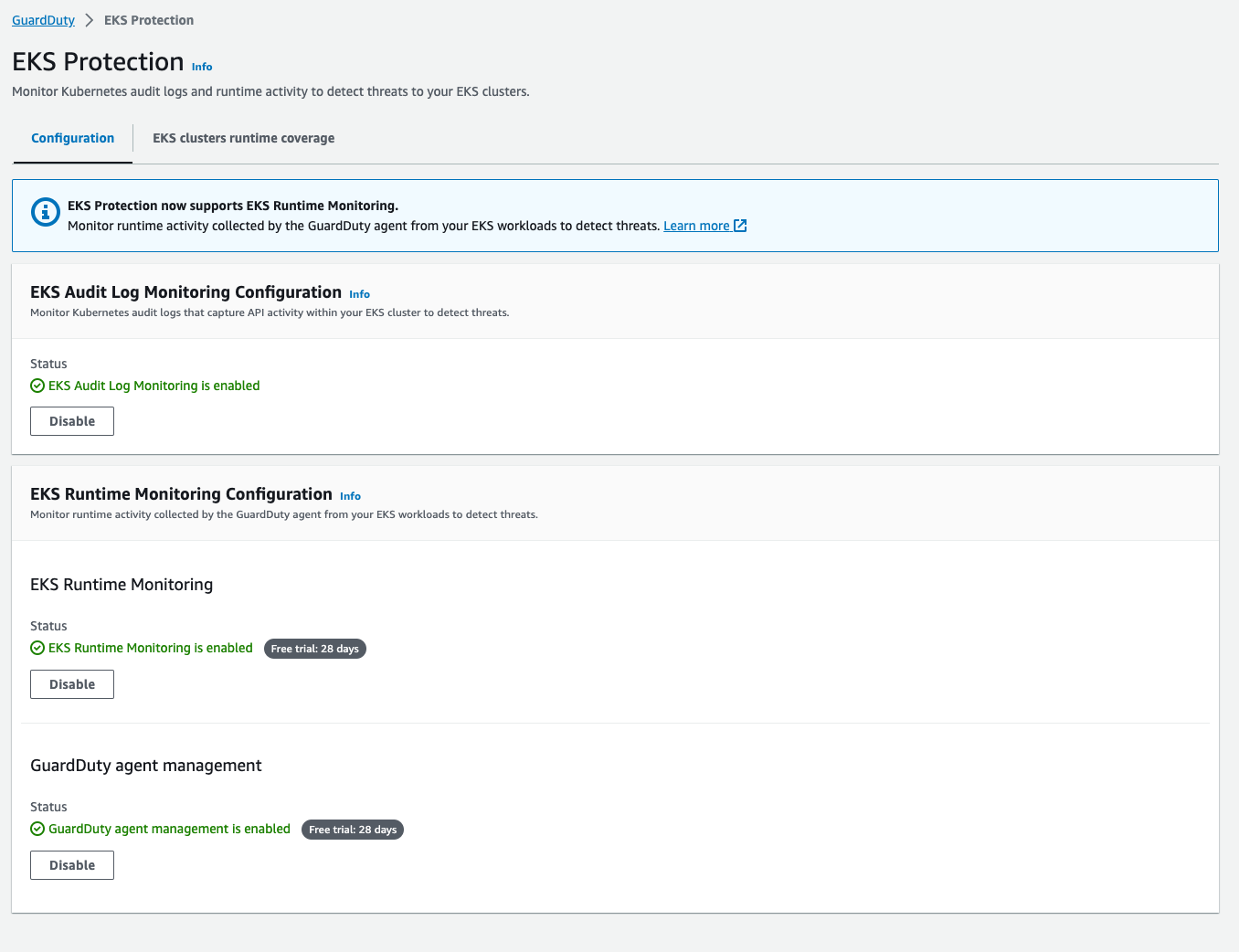
Configure GuardDuty Settings:
- Enable EKS Protection Runtime Monitoring
- Enable EKS Protection Audit Log Monitoring
Enable GuardDuty for EKS:
- Open the Amazon EKS console.
- Select your EKS cluster.
- In the navigation pane, choose "Add-ons."
- Find the Amazon GuardDuty add-on and choose "Enable."
- Wait for GuardDuty agents enrolled.
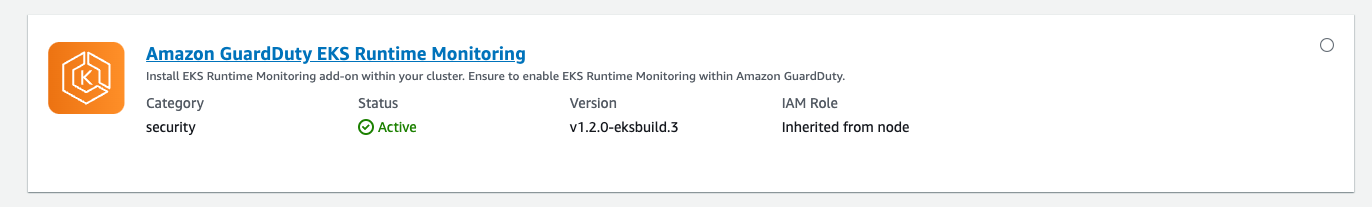
Configure EKS Integration:
- Follow the on-screen instructions to configure the integration between EKS and GuardDuty.
- This may involve granting necessary permissions and specifying the GuardDuty detector you created earlier.
Review and Monitor:
- Check GuardDuty EKS protection cluster coverage status. It should be healthy.
- After checking GuardDuty for your EKS cluster, regularly review the findings and alerts generated by GuardDuty to address any security concerns.
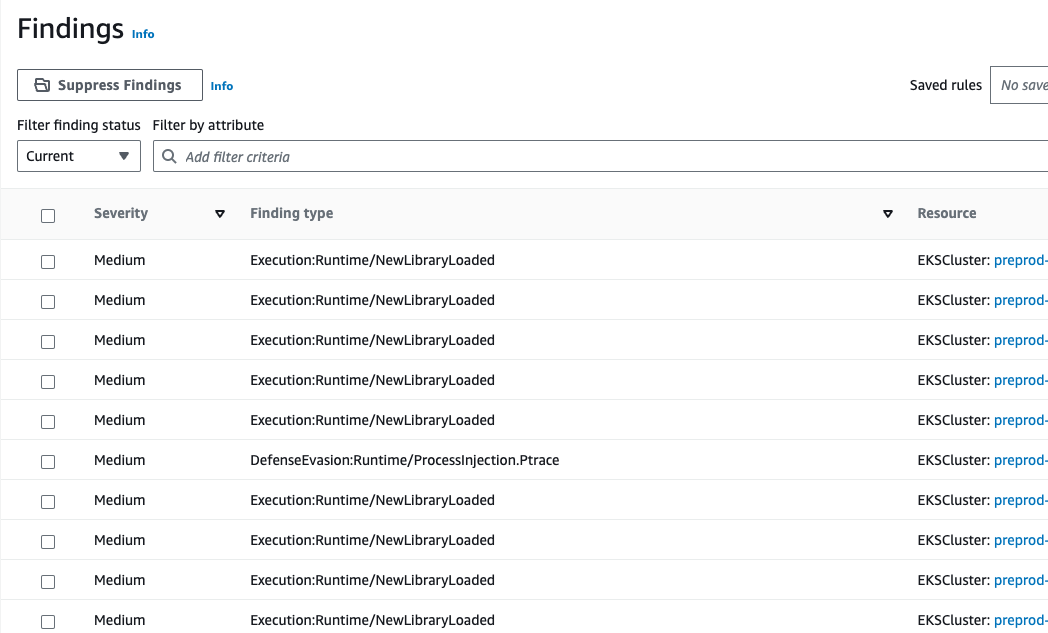
Description of GuardDuty Finding for EKS Protection
There are some findings above and they all have a meaning;
NewLibraryLoaded: created or recently modified library loading process.
ProcessIncection.Ptrace: ptrace system call was detected in a container or node.
More findings and explanations can be found here.
Extending GuardDuty to All Accounts in an AWS Organization:
To enable GuardDuty for all accounts under an AWS Organization, you can follow these steps:
Enable GuardDuty on the Organization Master Account:
- Log in to the AWS Management Console using the master account of the AWS Organization.
- Enable GuardDuty for the organization master account following the steps mentioned earlier.[Enable Amazon GuardDuty Service, Configure GuardDuty Settings]
- Also When enabled GuardDuty in the organization master account, On the Settings page, you need to add the GuardDuty delegated administrator account that you want for the organization.
- Enable EKS GuardDuty protection addons for each account EKS cluster following the steps mentioned earlier.
[Enable GuardDuty for EKS]
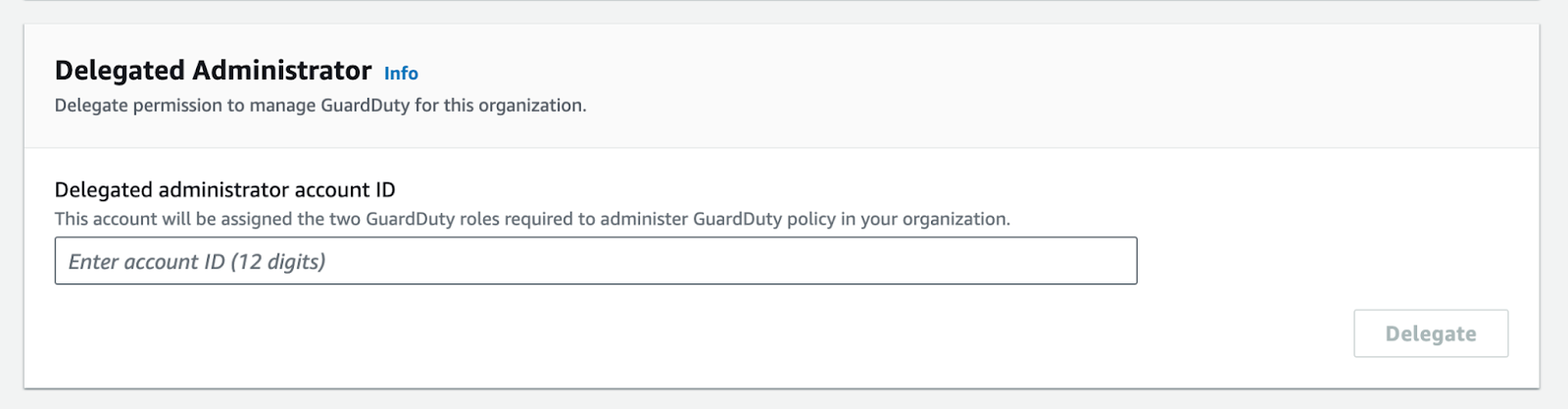
Invite Member Accounts:
- From the AWS Organizations console, invite the member accounts to enable GuardDuty.
Accept Invitations in Member Accounts:
- Log in to each invited member account.
- Accept the GuardDuty invitation from the master account.
Enable GuardDuty in Member Accounts:
- In each member account, enable GuardDuty following the same steps outlined earlier.
GuardDuty EKS Protection Pricing (as of September 2023)
The pricing structure for EKS Protection is divided into three tiers based on the volume of events generated per month as seen above table.
|
EKS Audit Logs |
|
|
First 100 million events / month |
$1.73 per one million events |
|
Next 100 million events / month |
$0.87 per one million events |
|
Over 200 million events / month |
$0.22 per one million events |
|
EKS Runtime Monitoring |
|
|
First 500 vCPUs / month (for monitored EKS instances) |
$1.50 per vCPU |
|
Next 4,500 vCPUs / month (for monitored EKS instances) |
$0.75 per vCPU |
|
Over 5,000 vCPUs / month (for monitored EKS instances) |
$0.25 per vCPU |
*** vCPUs per month for an instance = (total hours a supported provisioned active EKS instance ) x Number of vCPUs on the instance / (number of hours in a month)
Conclusion
In a rapidly evolving threat landscape, safeguarding your containerized workloads is paramount. Amazon GuardDuty, a powerful security service, extends its capabilities to Amazon EKS (Elastic Kubernetes Service) environments, enhancing protection against security risks and unauthorized access. By leveraging advanced machine learning algorithms and AWS's comprehensive threat intelligence, GuardDuty for EKS brings real-time threat detection to the world of containers.
EKS Audit Log Monitoring empowers administrators to maintain a proactive stance against potential breaches by analyzing audit logs for unauthorized access attempts, sensitive resource access, and changes to cluster configurations. The insights gained enable swift response and mitigation strategies to counter security threats.
EKS Runtime Monitoring takes a comprehensive approach by delving into the runtime environment of EKS clusters. It identifies unusual process activities, privilege escalations, and network connections that might indicate malicious intent. With detailed insights into CPU and memory usage patterns, administrators can ensure resource integrity and prevent potential attacks.
The integration of GuardDuty with EKS is not just about protection; it's about staying ahead of threats. By offering granular findings for different security aspects of your EKS clusters, GuardDuty aids in informed decision-making and rapid response to potential incidents.
For organizations looking to ensure a holistic security posture, GuardDuty's detailed findings provide actionable intelligence. Whether it's unauthorized access attempts, abnormal process behavior, or sensitive resource access, GuardDuty arms administrators with the information needed to fortify their EKS environments.
By following the steps outlined to extend GuardDuty protection across your AWS Organization, you can ensure that security is not just a concern of a single account but a comprehensive strategy embraced throughout your organization's accounts.
As you embark on your journey to secure containerized workloads with Amazon GuardDuty and EKS, remember that vigilance is the key to success. Regularly monitoring GuardDuty findings, staying updated with evolving threat landscapes, and continuously refining security practices will collectively contribute to maintaining a robust and secure containerized infrastructure on AWS.
Halil Bozan
Infrastructure and Platform Developer at kloia

