AWS Site-to-Site VPN vs. Transit VPC for Multi-VPC Connectivity
By design, securely connecting more than one VPC and on-premise network is a basic need for enterprise architectures in cloud networking. Within AWS, you can do this with AWS Site-to-Site VPN automatically or with Transit VPC manually. While both solutions enable communication between the on-prem center and the VPC, there are mild discrepancies between them in terms of design, management, scalability, and costs.
I will discuss the pros and cons of each method in this blog and highlight some of the factors that you would need to consider to make an informed decision about which one better fits into your architecture.
TL;DR;
- AWS Site-to-Site VPN is a managed solution offering:
- Easy scaling across multiple VPCs and regions,
- Built-in high availability (HA) with automatic failover,
- Lower management overhead and cost compared to third-party solutions,
- Simplified routing and network management via Transit Gateway
- Transit VPC makes use of third-party VPN appliances:
- Manual setup and management,
- Complicated and costly due to the requirements set for licensing and automation,
- Flexible but brings operational complexity,
- Security or some compliance requirements.
Conclusion: For most modern architectures, AWS Site-to-Site VPN is simpler, more scalable, and cost-effective while Transit VPC is better suited for specialized or legacy setups.
What is AWS Site-to-Site VPN?
AWS Site-to-Site VPN enables you to set up an encrypted IPSec connection among your on-premises network (or any other cloud provider) and an AWS VPC.
This connection is configured at the VPC degree. Site-to-Site VPN is designed for environments where you need to join an on-premises network to AWS, or maybe connect to more than one AWS region.

In other words, AWS Site-to-Site VPN is a managed solution that provides secure, scalable, and cost-effective cloud connectivity between your on-premises networks and AWS. It includes the following:
- Encrypted IPSec tunnels for secure communication.
- Flexibility in routing choices, including static and dynamic routing.
- Simplified management when integrated with AWS Transit Gateway.
- Built-in high availability for reliable, fault-tolerant connections.
- Dead Peer Detection (DPD) for automatic failover in case of network issues.
- CloudWatch monitoring for real-time visibility and alerts.
- Cost savings related to removing third-party appliances and simplifying management.
I mentioned only one-to-one VPN connection but you can manage multiple customer data centers to the same VPC or make your AWS VPC a main router for routing between multiple customer sites (VPN CloudHub).

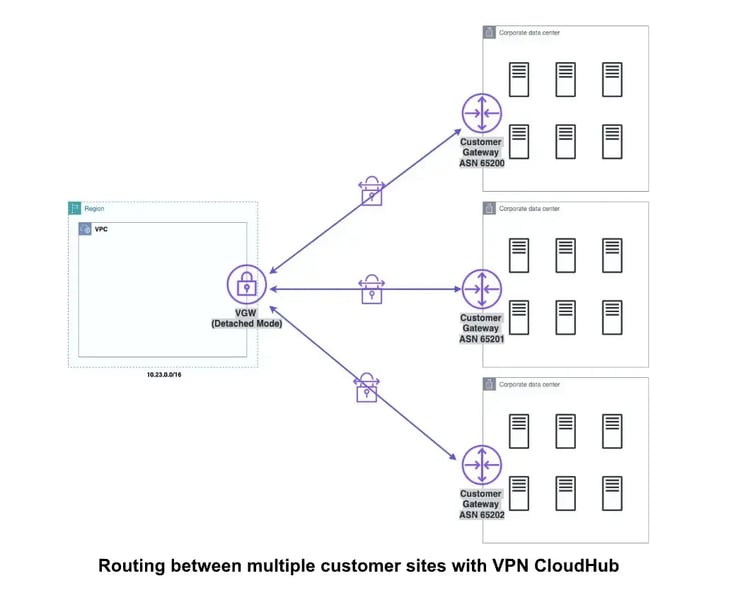
What is Transit VPC?
The Transit VPC is an architectural pattern that was developed to route traffic between multiple VPCs and on-premises networks through a central VPC hub. All of these hubs use third-party VPN appliances like Cisco or Palo Alto to manage network traffic.
Looking closely, the basic Site-to-Site VPN architecture involves the connection of one VPC with multiple data centers. In the real world, there may also be several VPCs connecting to one data center or even multiple data centers. Using Site-to-Site VPN in such cases introduces additional management complexities in maintaining connectivity and routing between these networks.

We are looking for a simplified solution where only one VPC hosts an on-premises VPN application on an EC2 instance. All VPN connections will need to terminate at this EC2 instance, effectively combining an AWS Managed VPN and an EC2-based VPN solution. Additionally, you would maintain VPN connections with your customer gateway. This setup represents a transit VPC architecture, which centrally connects multiple networks.

Transit VPC provides;
- Transit VPC uses a hub-and-spoke architecture where a central VPC routes traffic between multiple VPCs and on-premises networks, simplifying connectivity.
- It relies on third-party VPN appliances like Cisco or Palo Alto, which provide advanced routing and security features not natively available in AWS. You can:
* Install and use Advanced Threat Protection softwares where traffic is routed.
* Use a different VPN protocol than IPSec like GRE or DMVPN.
- By centralizing routing, Transit VPC reduces the complexity of managing multiple VPN connections through a single, central VPC for all traffic.
- You can use overlapping network addresses with Transit VPC which acts as a NAT translation IPs to different ranges to enable communication.
- You can create a Client-to-Site VPN where client devices can connect to Transit VPC EC2 instances by establishing VPN connection.
|
Feature |
AWS Site-to-Site VPN |
Transit VPC |
|
Architecture |
Managed by AWS, no need for third-party appliances. |
Requires third-party VPN appliances in a hub VPC. |
|
Scalability |
It can scale, but it would be better with Transit Gateway, as it supports thousands of VPCs. |
Scaling is manual and complex, often requiring Lambda automation. |
|
Cost |
Costs include VPN data transfer fees and Transit Gateway charges (if applicable). |
High cost due to VPN appliances (license fees) and data transfer charges. |
|
High Availability (HA) |
Built-in HA through multiple AWS Availability Zones (AZs). |
HA requires setting up redundant VPN appliances, adding complexity. |
|
Performance |
Managed VPN performance, typically 1.25 Gbps per VPN tunnel. |
Dependent on third-party appliances, which can limit performance. |
|
Security |
Fully managed by AWS with IPSec encryption. |
Security is managed by the third-party appliance (firewall/VPN). |
|
Management |
Easy to manage through AWS Console and Transit Gateway. |
Requires managing third-party appliances, routing, and complex automation scripts. |
|
Routing Flexibility |
Supports dynamic routing (BGP) |
Provides flexible routing but requires manual configuration. |
|
Cross-Region Support |
Natively supported with AWS inter-region peering. |
Supported, but manual configuration and appliance setup are required. |
Key Considerations
Management
AWS Site-to-Site VPN: When integrated with AWS Transit Gateway, the management overhead is significantly reduced. AWS handles much of the complexity, and VPN connections can be easily monitored, scaled, and automated using native AWS tools like the Console, CloudWatch, and Route 53.
Transit VPC: Transit VPC is more manual in nature. You’ll need to deploy and manage third-party VPN appliances, which often require complex automation scripts (like AWS Lambda) to create and tear down VPN connections as needed. If your VPN appliance experiences issues or goes down, you’ll need to troubleshoot both AWS and third-party services.
Cost Efficiency
AWS Site-to-Site VPN: Costs for AWS Site-to-Site VPN primarily come from data transfer charges and the fees associated with AWS Transit Gateway (if used). Since there’s no need to maintain third-party VPN appliances, overall management and licensing costs are lower. Transit Gateway also reduces cross-VPC data transfer costs compared to VPC peering.
Transit VPC: Transit VPC architecture can be significantly more expensive, especially with VPN appliances that require additional licensing, maintenance, and support.
Performance
AWS Site-to-Site VPN: AWS VPN performance is relatively straightforward—each VPN tunnel offers up to 1.25 Gbps of throughput.
Transit VPC: The performance in Transit VPC architecture depends heavily on the performance and capabilities of the third-party VPN appliances.
High Availability
AWS Site-to-Site VPN: High availability is a native feature of AWS Site-to-Site VPN when used with AWS Transit Gateway. VPN connections automatically failover between Availability Zones if an issue arises, providing seamless availability.
Transit VPC: You must manually configure high availability by deploying redundant VPN appliances across multiple AZs. This adds complexity to the architecture and requires additional automation to ensure failover works properly.
When to use what?
AWS Site-to-Site VPN, especially when used with AWS Transit Gateway, is ideal if you’re looking for a fully managed solution with built-in scalability and availability. It is the best choice for enterprises that need to scale VPN connections across multiple VPCs and regions, without the overhead of managing third-party appliances.
The Transit VPC architecture might still be a good choice in specialized cases where third-party VPN appliances are necessary due to specific security requirements, compliance needs, or if you already have significant investments in third-party networking tools, or you need to accept overlapping network addresses for requirment.
Conclusion
While both AWS Site-to-Site VPN and Transit VPC can be used for connecting multiple VPCs and on-premises networks, AWS Site-to-Site VPN—particularly when paired with AWS Transit Gateway—offers a more streamlined, scalable, and cost-effective solution for most scenarios. Transit VPC, while flexible, often brings increased complexity and higher costs due to the need for third-party appliances and manual configuration.
Choosing the right solution depends on your specific networking requirements, performance needs, and operational preferences. For most modern cloud architectures, AWS Site-to-Site VPN with Transit Gateway provides a simpler, more cost-efficient way to manage multi-VPC connectivity at scale.
Ahmet Arif Özçelik
Platform Engineer @kloia