Lacework vs AWS Security Services
With the prevalence of cloud computing, we are able to build our apps that scale quicker all over the world, more redundant, and more cost-effective. To understand the predominance of cloud services, take a quick glance at Gartner's 2022 report:

Security is one of the critical topics that is being overlooked as cloud computing becomes more popular. While businesses transition to the cloud, they may believe that security concerns are solely the responsibility of cloud providers. To avoid making this error, we should study the shared responsibility model.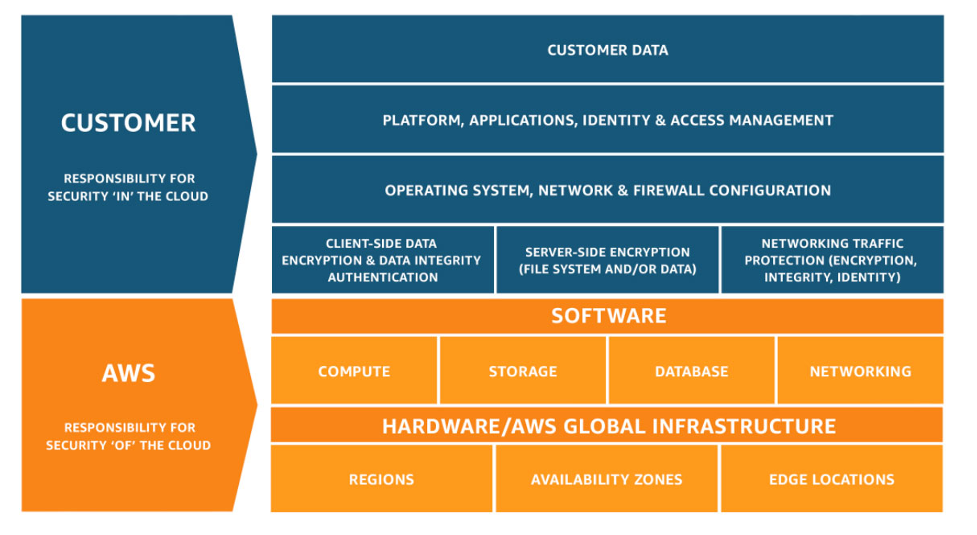
This diagram is published by AWS and can be seen here. We can identify which security-related concerns are under our control by looking at this model. If we list the most typical cloud security mistakes;
- NotLeastPrivilige means FullAccess :D
- Hard-coded credentials
- Using long live credentials
- Public Endpoints like Public S3 Buckets
- Publicly Open Ports
- Unencrypted data
- Lack of compliance
- Lack of monitoring
- Bad network design
- Not patching vulnerable packages and OS
And the list continues…

But how can we meet all of these security requirements? How can we be alerted when someone violates our rules? How can we centrally monitor all environments, rules, systems, and regions from a single location? How can we identify when there is an anomaly with the system?
This is where Lacework comes to our rescue. Lacework collects and evaluates cloud security metrics and data. This allows you to monitor your cloud security status from a single location. You can view these in the UI and create different alarms and reports.
In this article, I will compare the differences and similarities between Lacework and AWS Security services. Then I'll discuss which one could be used in different scenarios.
I’ll compare Lacework with GuardDuty, Inspector, Config, and Security Hub.
Lacework vs Amazon GuardDuty
Amazon GuardDuty is a threat detection service that continuously monitors data sources, such as AWS CloudTrail data events for Amazon S3 logs, CloudTrail management event logs, DNS logs, Amazon EBS volume data, Amazon EKS audit logs, and Amazon VPC flow logs for malicious activity and unauthorized behavior to protect your Amazon Web Services accounts, workloads.
|
Lacework |
Amazon GuardDuty |
|
|
Predefined rules |
Rules Optional Anomalous Detections (Detect unknown unknowns + known bads) |
AWS developed ruleset against threats common to all AWS customers using known attack tactics |
|
Region |
Builds a model for every AWS account for workloads in all regions |
Region-specific service. Needs to be enabled in all 21 regions of an account. Findings are isolated to region |
|
Investigation |
Investigation built into the alerting |
Uses AWS Detective for further investigation |
|
Agent |
Application/Container/K8s visibility = Agent |
Application/container/host visibility requires additional tools and a different interface |
Lacework vs Amazon Inspector
Amazon Inspector is a vulnerability management service that continuously scans your AWS workloads for vulnerabilities. Amazon Inspector automatically discovers and scans Amazon EC2 instances and container images residing in Amazon Elastic Container Registry (Amazon ECR) for software vulnerabilities and unintended network exposure.
|
Lacework |
Amazon Inspector |
|
Run time protection to detect compromised instances for container-based applications |
Easy setup in the AWS Console (a few clicks) |
|
Data aggregation across instances in all regions |
Continuous scanning for vulnerabilities on hosts and in container images in ECR |
|
OS package manager installed software plus Non-OS language libraries scanned (i.e. packages installed with pip, npm, etc.) for containerized workloads |
At launch, doesn’t support Windows OS for EC2 or distroless container images |
|
Vulnerabilities in container registries are correlated with containers running in your environment |
No correlation between vulns in ECR and running containers |
Lacework vs AWS Config
AWS Config is a cloud auditing service that offers an inventory of current resources as well as tracking AWS resources to examine compliance and security levels.
|
Lacework |
AWS Config |
|
Learns user and entity behavior (UEBA) for each account and alerts when anomalous behavior occurs |
Rules-based approach to discovering when resource configuration has changed |
|
Config and compliance are out of the box features |
Provides information about whether your resources are compliant with configuration rules you specify |
|
After account integration, all activity is available in all regions |
Regional service that needs to be enabled in every account and every region |
|
Discovery and detection made easy with high context events for troubleshooting and remediation |
Easy tracking for change management |
Lacework vs AWS Security Hub
AWS Security Hub collects and compares security data from AWS services and other vendor security services to best practices and compliance standards.
|
Lacework |
AWS Security Hub |
|
Platform approach to security with aggregated data for all your AWS accounts |
Single place that aggregates, organizes, and prioritizes your security alerts or findings from multiple AWS services and vendor services |
|
Provides customer-centric evaluation of your security posture with baseline behavioral analytics |
Trying to bring “single-pane-of-glass” consolidation of scattered security tools |
|
Multiple accounts supported after integrations are set up with multi-region resource assessment |
Region-based service, which must be set up in every individual region you may have workloads in |
Conclusion
Lacework may be handy if you are working with more than one cloud provider and have many environments. From a centralized place, you can monitor the security status of all environments and cloud providers. However, if you simply use AWS, AWS Native services will function. You can receive data from other accounts if you define an account as a security account and make it a delegated administrator.
Emre Oztoprak
Emre is a Cloud Engineer at Kloia. He is working on mainly AWS, Cloud Native, and Serverless technologies. He is also interested in cloud security.
